Context
I am using a REST API Resource to interact with my interface-less API backend and use Retool to build an administration section.
Situation
I want to let my Retool users download a file which is exposed behind a secured endpoint on my backend (through authorization header) which does a URL Redirection (HTTP 302) to a temporary public url.
HTTP Response of the REST API
curl -I https://my-backend-api.com/report -H 'Authorization: MyAuthorizationToken'
HTTP/1.1 302 Found
Server: Cowboy
Date: Mon, 22 Nov 2021 12:40:42 GMT
Referrer-Policy: strict-origin-when-cross-origin
Location: https://mybucket.s3.eu-west-1.amazonaws.com/myobject?aws_specific_auth_query_params ⬅️ *A temporary public URL*
Issues
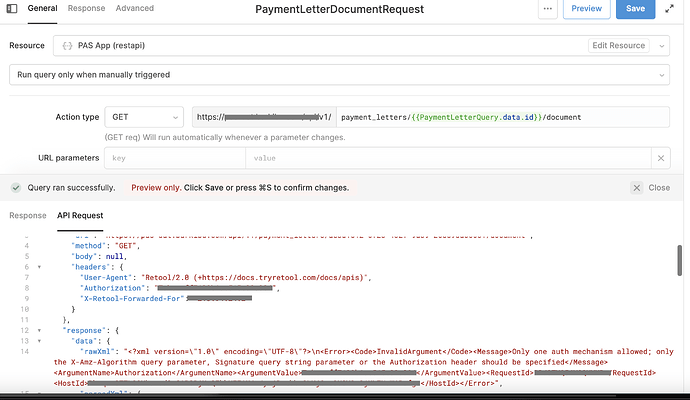
I encounter two problems here. The Query that I am building on Retool is automatically following the redirect and is leaking the authorization header by forwarding it to the redirect url.
Expected Behaviour
The headers are not forwarded
I can choose whether I want the query to follow the redirect or not and pick up the location myself in the metadata.
Help Needed
- Am I missing something that might explain Retool's Query implementation choice of forwarding the headers ?
- Am I missing a way to achieve my goal of requesting to my backend the generation of a temporary URL using the configured REST API Resource and access the response before the redirect ?