We're currently using Custom Auth with OAuth2 generic flow to authenticate and authorise with our Azure AD and APIs. But the id token we use in this flow expires after 1 hour. At the moment it's not easy for us to change this expiration period so we'd like to explore if we can use refresh tokens in Custom Auth OAuth2 generic flow? Is there any documentation regarding this flow?
Did you ever manage to figure this out? Currently doing the same with Azure AD and don't have the Refresh Token working.
This documentation should prove helpful for what you're trying to setup: https://docs.retool.com/docs/sso-generic-openid-provider#using-the-jwts-obtained-from-the-auth-flow-in-resources
This doesn't really answer the question - Retool doesn't seem to request a refresh token when requesting the initial access token.
Hey @alec-hs - happy to help! So, the documentation I shared answers the initial question of
At the moment it’s not easy for us to change this expiration period so we’d like to explore if we can use refresh tokens in Custom Auth OAuth2 generic flow? Is there any documentation regarding this flow?
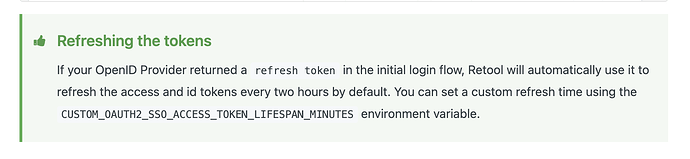
Those docs highlight the environment variable CUSTOM_OAUTH2_SSO_ACCESS_TOKEN_LIFESPAN_MINUTES which can help with extending the expiration period:
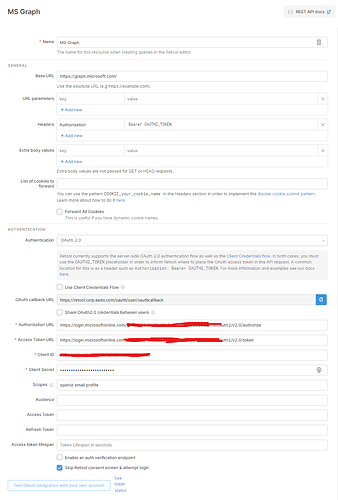
As for Retool not requesting a refresh token when requesting the initial access token, could you share a screenshot of your resource configuration page so that we can further debug it?
@Jay any ideas on this?
Hi all, stepping in here with Jay to try to help!
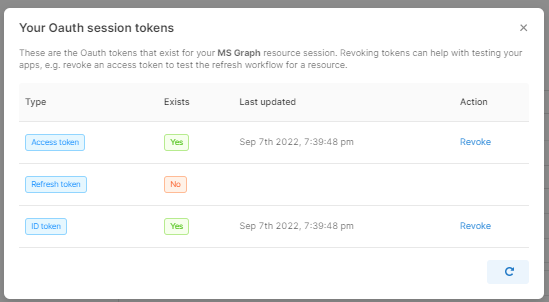
For context, Retool can only automatically refresh if ONLY the access token is expired and the refresh token is not. You'd need to go through the auth flow if the refresh token is expired.
Do you know how your endpoint deals out refresh tokens?
I'm having the same issue as @alec-hs. When using OAuth2 with Azure AD Retool does not seem to save the refresh token for some reason. This is an example of the response from the access token URL taken from here:
{
"token_type": "Bearer",
"scope": "user.read%20Fmail.read",
"expires_in": 3600,
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIng1dCI6Ik5HVEZ2ZEstZnl0aEV1Q...",
"refresh_token": "AwABAAAAvPM1KaPlrEqdFSBzjqfTGAMxZGUTdM0t4B4..."
}
@emileriksen thank you for sending that over! This looks like a bug on our end, perhaps related to the way we're handling scopes or the refresh flow when using OAuth2 with Azure AD in general. I'm asking about a workaround now, will keep you posted.
Would you be able to try using Custom Auth instead of OAuth2 to get this setup? Or do you know if you're able to manually pass in the scopes you need for the refresh flow?
Thank you for your reply! Setting up custom auth is not really worth the effort. It's not that bad of an issue having to authenticate often - just a little annoying so if it's a bug that will be fixed, I'd rather just wait for the fix ![]()
Sounds like a plan! I'll keep you updated ![]()
I have this issue too. Is there a proper solution for setting up OAuth2 to Azure AD apps? Documentation is really unclear. I've tried the Custom Auth option too and same issue. No way to get a refresh token...even with a second step. It seems like there's a bug that prevents passing variables in Custom Auth? Thanks.
Hey @corytomlinson! Do you mean this sort of Azure AD available on Enterprise plans? Either way, would you mind sharing a screenshot of your current resource page setup? ![]()
@victoria was there any update to this original issue? Not for SSO users but just for OAuth refresh tokens not being saved.
Not sure if this directly answers your question, but this is what we heard back when checking in ![]() It seems like you should be able to pass scopes for the refresh endpoint in custom auth. These accept any inputs since this is a simple request form. Are you interested in/able to pass scopes in the refresh request?
It seems like you should be able to pass scopes for the refresh endpoint in custom auth. These accept any inputs since this is a simple request form. Are you interested in/able to pass scopes in the refresh request?
@alec-hs not sure if it is applicable to your situation but in our project we're using Duende Identity Server and it was necessary to add the 'offline_access' scope to retrieve a refresh token