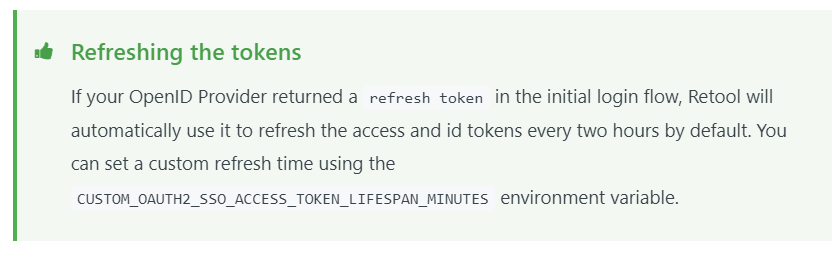
We are using OpenID Connect SSO with Azure AD to authenticate users for Retool. We are passing back the same access token that Retool uses for SSO in order to authenticate to our REST Api, using %USER_OAUTH2_ACCESS_TOKEN%, as documented here:
https://docs.retool.com/docs/sso-generic-openid-provider#using-the-jwts-obtained-from-the-auth-flow-in-resources
Our REST API successfully accepts the token provided when the user initially authenticates into Retool.
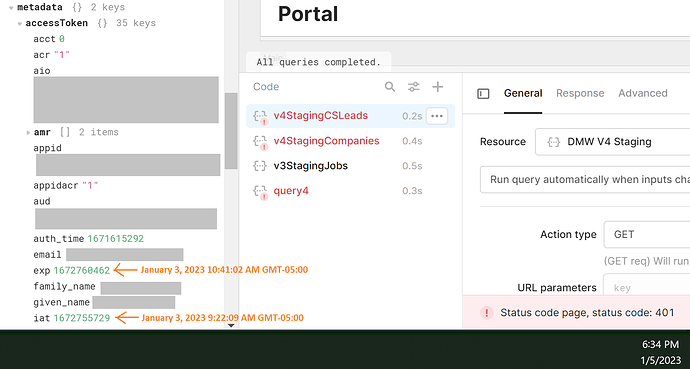
However, if a user returns to the Retool browser window after a couple of hours, our API returns 401 errors because the token has expired. When examining the current_user global in Retool, the accessToken also shows as expired (the value of exp is in the past). This makes it seem that Retool is not refreshing the access token, even though the documentation linked above seems to indicate that Retool will refresh the tokens automatically.
Setting CUSTOM_OAUTH2_SSO_ACCESS_TOKEN_LIFESPAN_MINUTES did not make a difference. Are we correct in expecting the tokens to be automatically refreshed or is there any other configuration that we are missing to enable a new valid access token to be sent with our API calls? We are running Retool version 2.103.7.
Thank you.