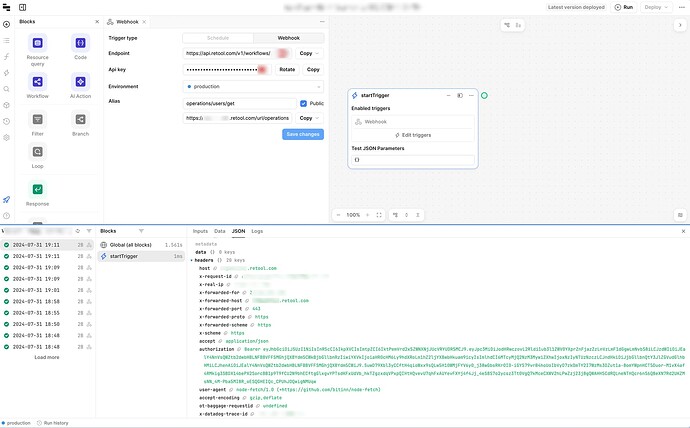
Well... after some dark magic, it works.
Quite honestly, I'm not sure why it works now. All of the configuration variables and resource setup are exactly the same as before.
Only thing I changed was my own Auth0 config, which initially did not authorize my Auth0 app with any Auth0 API—seemingly a requirement for returning an access token from the /oauth/token endpoint. Amateur problems.
This allowed me to verify my Auth0 access token endpoint and authenticate with my API locally.
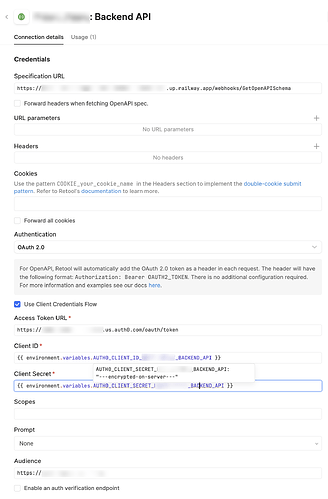
Unfortunately, the Auth0 config change didn’t solve my problem: Retool wasn’t successfully returning a token from the endpoint I just verified locally—at least not when using a secret config variable for the Client Secret field.
But eventually, after:
-
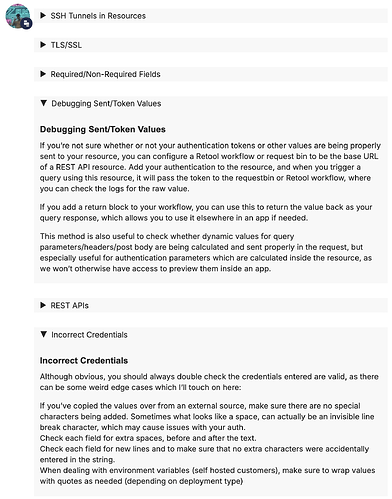
Following the "Debugging Sent/Token Values" instructions here
-
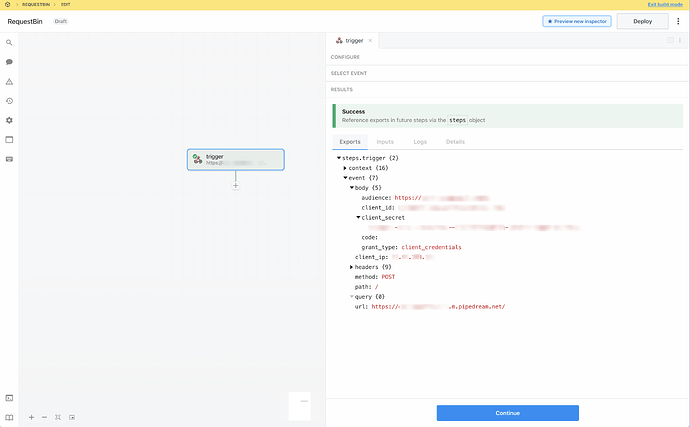
Using Requestbin as the Access Token URL (since Retool Workflows doesn't seem to expose the auth headers) to inspect the auth headers (specifically client secret) sent from the Retool OpenAPI resource configuration
-
Using a Retool workflow as the server url in my OpenAPI spec (i.e. I added a public Retool workflow endpoint as the "server url" in the spec)
...to inspect the Bearer Token
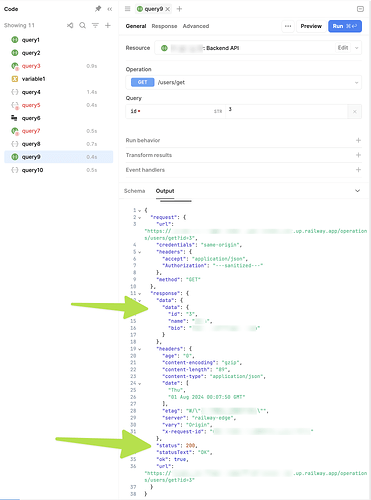
I was eventually able to confirm that both the Client Secret (in a secret Retool Configuration variable) and the Bearer Token were being correctly passed.
That confused me, since nothing really changed but the endpoints. So I went back to the resource, changed the endpoints back to the real ones, hit save 10+ times, reloaded my test app, and authentication went through 


TLDR;
Not sure if this was just me missing something simple or if "jiggling" the problem just made it work? But if anyone else comes across this issue, I hope this helps!
Below was my draft post of things I was trying before everything just worked, if helpful for Retool team or to spare anyone else from trying the same 
Another Update
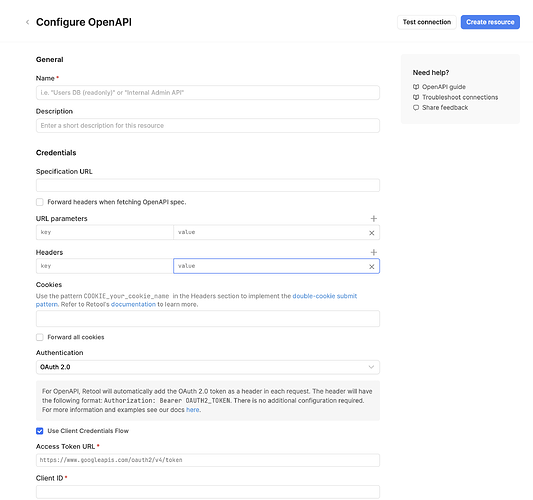
I was able to isolate the problem down to using secret Configuration Variables in the OpenAPI resource:
- Pasting the client secret as plaintext into the Client Secret field on the OpenAPI resource works fine! But, that's bad bad
 :
:
- Creating a not-secret configuration variable for the Client Secret also works fine! But... also not good

- I tried encoding the client secret as base64 (both url-friendly and not) before adding it to a secret Config variable. No luck

- I tried wrapping the secret config variable in a template string. No luck

{{ `${environment.variables.AUTH0_CLIENT_SECRET_MAGIC_APPLY_BACKEND_API}` }}
- I tried trimming the whitespace. Nada.
{{ environment.variables.AUTH0_CLIENT_SECRET_MAGIC_APPLY_BACKEND_API.trim }}
Again, the REST API resource does not have this issue. Using secret config variables does not cause any issues in the REST resource.
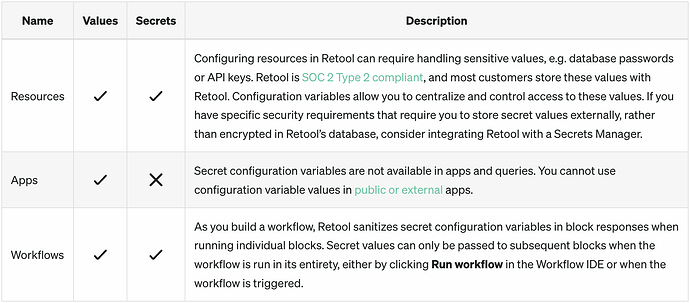
So given the above, I would disqualify the limitations on secret config variables listed here as the issue:
And I'm left thinking...