I have a development environment self-hosted instance of Retool running via docker-compose on ec2.
For this PoC I have the temporal cluster also running on the same ec2 instance.
In other words this is the docker-compose file I'm using, without modification, except for what I'm about to describe next for the code-executor service.
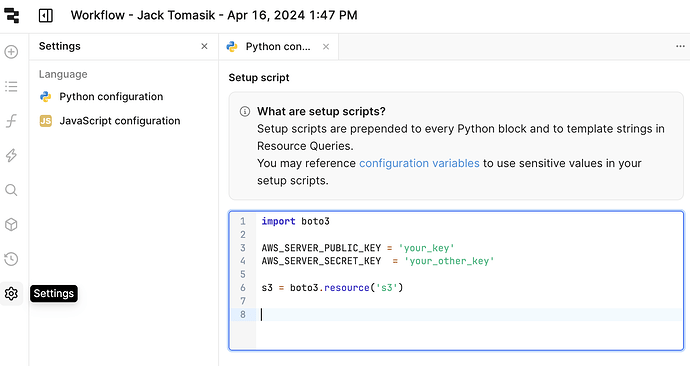
If I create a workflow with a block that uses the boto3 sdk, I get an error message Unable to locate credentials.
I found this similar report which informed me that nsjail running in privileged mode will not be able to reach the metadata service at 169.254.169.254 to automatically authenticate boto3.
Ideally, when I get to the production version of self-hosted Retool, I'll need to use an IAM role adhering to the principle of least privilege, so if possible, I'd like to find a way to set up workflows to authenticate with boto3 while sandboxing the code.
However, for the sake of trying to move forward on the development instance, I've attempted to remove nsjail from the equation.
I've updated the environment variables and privilege to false per the documentations' instructions.
code-executor:
build:
context: ./
dockerfile: CodeExecutor.Dockerfile
command: bash -c "./start.sh"
env_file: ./docker.env
environment:
- CONTAINER_UNPRIVILEGED_MODE=TRUE <----- added this
- DISABLE_IPTABLES_SECURITY_CONFIGURATION=TRUE <----- added this
- DEPLOYMENT_TEMPLATE_TYPE=docker-compose
- NODE_OPTIONS=--max_old_space_size=1024
networks:
- code-executor-network
# code-executor uses nsjail to sandbox code execution. nsjail requires
# privileged container access.
# If your deployment does not support privileged access, you can set this
# to false to not use nsjail. Without nsjail, all code is run without
# sandboxing within your deployment.
privileged: false <----- was true
restart: on-failure
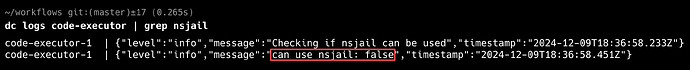
Strangely, with this docker-compose configuration, I get an odd error message saying the container is running in privileged mode. ![]()
By some random chance I decided to switch from TRUE to true
which changes the reported error message.
I'm surprised the case of the value is load-bearing.
CONTAINER_UNPRIVILEGED_MODE=TRUE
DISABLE_IPTABLES_SECURITY_CONFIGURATION=TRUE
to
CONTAINER_UNPRIVILEGED_MODE=true <----- lowercase
DISABLE_IPTABLES_SECURITY_CONFIGURATION=true <----- lowercase
I'm hoping I can get help with the following:
- What does retool mean when it says the user running container is not the expected user, retool_user in retool_user group? This approach is me forcing the unsandboxed solution, but is not suitable for production.
- How do I authenticate boto3, either automatically by the metadata service or manually by providing environment variables into the config.
- If I'm going the environment variable route, could someone from retool enable those beta feature flags for my account.
Thanks in advance for the help.