Hey,
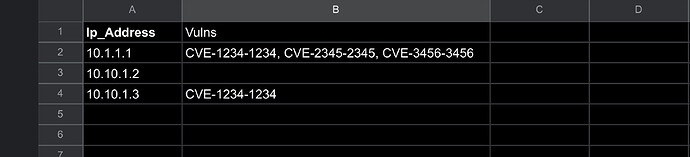
I am returning data via dynamo db and populating a table with the output.
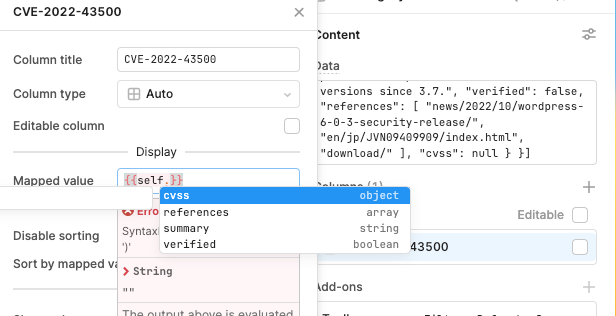
One of the columns contains nested JSON. What I am trying to achieve is extracting the key values and displaying them as a comma-separated list.
I don't need to access the other fields such as summary.
See the string below for an example of the nested JSON, I am looking to extract just CVE-1234-1234, CVE-3456-3456 etc and display it as a comma-separated list in the row.
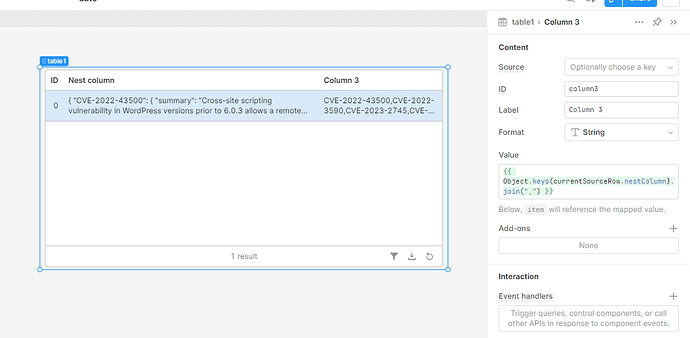
Hoping someone can help, I have no idea how to approach this, I assume using map or a transformer but JS is not my strong point.
Here is an example of the data:
{ "CVE-2022-43500": { "summary": "Cross-site scripting vulnerability in WordPress versions prior to 6.0.3 allows a remote unauthenticated attacker to inject an arbitrary script. The developer also provides new patched releases for all versions since 3.7.", "verified": false, "references": [ "news/2022/10/wordpress-6-0-3-security-release/", "en/jp/JVN09409909/index.html", "download/" ], "cvss": null }, "CVE-2022-3590": { "summary": "WordPress is affected by an unauthenticated blind SSRF in the pingback feature. Because of a TOCTOU race condition between the validation checks and the HTTP request, attackers can reach internal hosts that are explicitly forbidden.", "verified": false, "references": [ "vulnerability/c8814e6e-78b3-4f63-a1d3-6906a84c1f11", "wordpress-core-unauthenticated-blind-ssrf/" ], "cvss": null }, "CVE-2023-2745": { "summary": "WordPress Core is vulnerable to Directory Traversal in versions up to, and including, 6.2, via the ‘wp_lang’ parameter. This allows unauthenticated attackers to access and load arbitrary translation files. In cases where an attacker is able to upload a crafted translation file onto the site, such as via an upload form, this could be also used to perform a Cross-Site Scripting attack.", "verified": false, "references": [ "news/2023/05/wordpress-6-2-1-maintenance-security-release/", "threat-intel/vulnerabilities/id/edcf46b6-368e-49c0-b2c3-99bf6e2d358f?source=cve", "/changeset?sfp_email=&sfph_mail=&reponame=&old=55765%40%2F&new=55765%40%2F&sfp_email=&sfph_mail=", "files/172426/WordPress-Core-6.2-XSS-CSRF-Directory-Traversal.html", "debian-lts-announce/2023/06/msg00024.html" ], "cvss": null }, "CVE-2022-43497": { "summary": "Cross-site scripting vulnerability in WordPress versions prior to 6.0.3 allows a remote unauthenticated attacker to inject an arbitrary script. The developer also provides new patched releases for all versions since 3.7.", "verified": false, "references": [ "2022/10/wordpress-6-0-3-security-release/", "/JVN09409909/index.html", "download/" ], "cvss": null }, "CVE-2022-43504": { "summary": "Improper authentication vulnerability in WordPress versions prior to 6.0.3 allows a remote unauthenticated attacker to obtain the email address of the user who posted a blog using the WordPress Post by Email Feature. The developer also provides new patched releases for all versions since 3.7.", "verified": false, "references": [ "/news/2022/10/wordpress-6-0-3-security-release/", "/jp/JVN09409909/index.html", "download/" ], "cvss": null }, "CVE-2023-22622": { "summary": "WordPress through 6.1.1 depends on unpredictable client visits to cause wp-cron.php execution and the resulting security updates, and the source code describes "the scenario where a site may not receive enough visits to execute scheduled tasks in a timely manner," but neither the installation guide nor the security guide mentions this default behavior, or alerts the user about security risks on installations with very few visits.", "verified": false, "references": [ "/WordPress/WordPress/blob/dca7b5204b5fea54e6d1774689777b359a9222ab/wp-cron.php#L5-L8", "/plugins/cron/", "/plugins/was/113449", "hecpanelguy/the-nightmare-that-is-wpcron-php-ae31c1d3ae30", "about/security/", "support/article/how-to-install-wordpress/", "/articles/solving-unpredictable-wp-cron-problems-addressing-cve-2023-22622/" ], "cvss": null } }