kimdal
August 12, 2021, 4:40pm
1
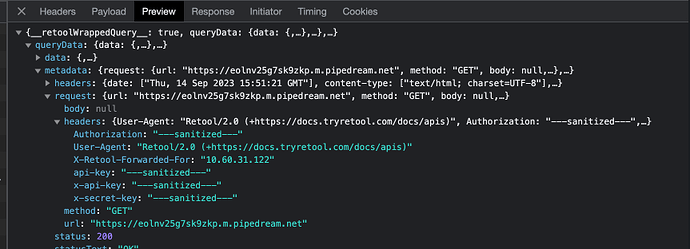
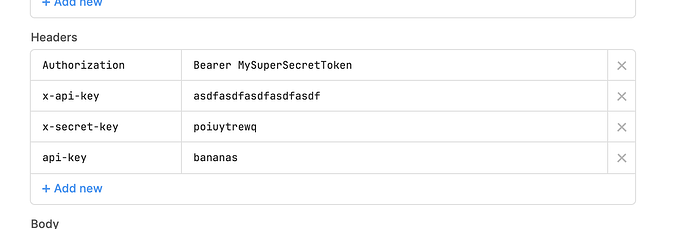
If I set the header of the resource like first image,
The "Authorization" header is sanitized, but others are completely exposed.
Many APIs use authentication via custom headers.
5 Likes
I'd like to second that. It should be possible to hide some of the headers that are set on a resource level from the the browser.
1 Like
Any updates/ideas on this?
Hey @nikcaryo-super !
These headers should now be sanitized, are you seeing differently?
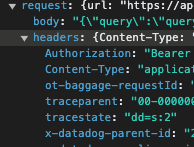
I don't see them sanitized. Is that a regression?
Hey @Manuel_de_la_Torre is this request coming from a cloud org? I'm unable to reproduce, but happy to take another look.
Yes, it's a cloud org (zenfi) in a Team subscription. I'm using a Bearer Token authentication on a GraphQL endpoint.
Should I open a support ticket?
@Manuel_de_la_Torre no need, we'll handle it here. Currently GraphQL requests are not sanitized, we were discussing REST API query requests above. We do have an internal ticket for sanitizing GraphQl as well, and we can update this post when we have any additional information on its status.
Thank you @joeBumbaca I hope it can be fixed soon. It represents a security issue for us, as well.