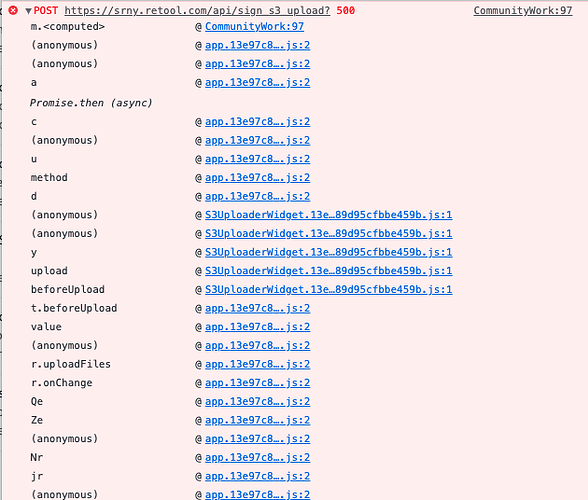
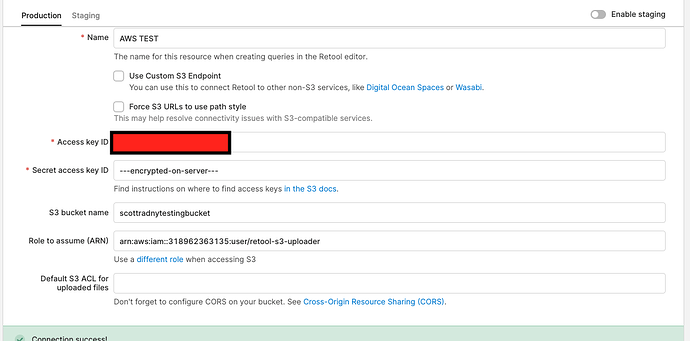
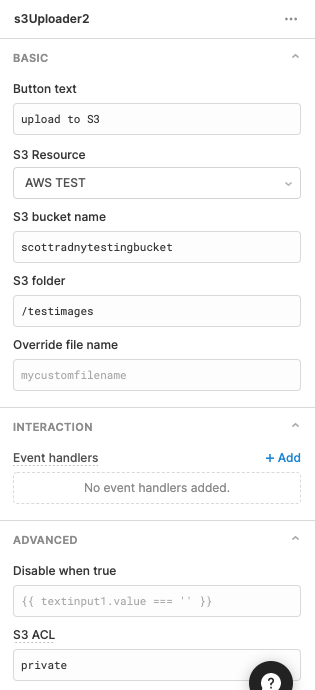
The documentation is seriously lacking. Here's how I was able to finally set up S3 with retool:
-
Create a new user in the IAM section let's assume retool-s3-user without assigning any permissions/roles.
-
Create your S3 bucket and attach the required CORS permissions:
[
{
"AllowedHeaders": [
"*"
],
"AllowedMethods": [
"PUT",
"POST",
"DELETE"
],
"AllowedOrigins": [
"https://*.retool.com"
],
"ExposeHeaders": []
},
{
"AllowedHeaders": [],
"AllowedMethods": [
"GET"
],
"AllowedOrigins": [
"*"
],
"ExposeHeaders": []
}
]
- Create a new role from IAM, let's say
retool-s3-assume-role and the following JSON for Trust Relationship/Trust Policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "s3.amazonaws.com",
"AWS": "arn:aws:iam::<AWS_ACCOUNT_ID>:user/retool-s3-uploader"
},
"Action": "sts:AssumeRole"
}
]
}
- Create a new policy let's say
retool-s3-policy and add the following JSON to create the policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketAcl",
"s3:GetBucketCORS",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketNotification",
"s3:GetBucketPolicy",
"s3:GetBucketWebsite",
"s3:GetObject",
"s3:GetObjectAcl",
"s3:GetObjectVersion",
"s3:GetObjectVersionAcl",
"s3:PutObject",
"s3:PutObjectAcl",
"s3:PutObjectTagging",
"s3:PutObjectVersionAcl",
"s3:PutObjectVersionTagging"
],
"Resource": [
"arn:aws:s3:::<BUCKET_NAME>",
"arn:aws:s3:::<BUCKET_NAME>/*",
"arn:aws:iam::<AWS_ACCOUNT_ID>:role/retool-s3-assume-role"
]
}
]
}
- Finally, attach the created policy
retool-s3-policy under the role retool-s3-assume-role