Hi,
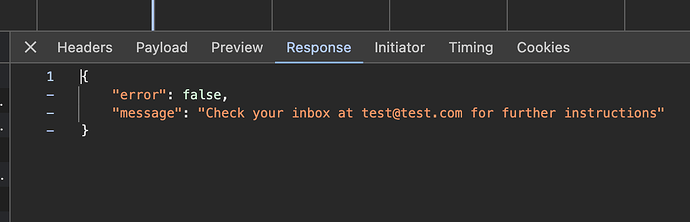
We have deployed a self-hosted instance of retool. Upon creating our organization, our password manager has not automatically saved the credentials. Therefore, we tried to use the password reset functionality of the application. In the network console, the request is a POST https://{ourDomain}/api/user/resetPassword and we receive a 200 response with the following message :
{
"error": false,
"message": "Check your inbox at email@ourdomain.com for further instructions"
}
The password reset email is never sent (or never reaches our inbox). Retool support could not help us and suggested we post here. Furthermore ...
- There are a few threads about this topic, but this case is not about Retool On-prem Portal portal - we can connect just fine on that platform and we know they use different sets of credentials
- We have validated with our DevOps team that the networking requirements were applied, including CIDR / Individual IPs / domains whitelisting (Self-hosted Retool requirements | Retool Docs). Our firewall allows traffic to leave the instance
- We have already checked to make sure the password reset wasn't in a spam/filtered box
- This is a docker deployment within Azure
- Our billing platform indicates a free plan, although the deployment (advanced -> billing) indicated that we were on enterprise even after sync'ing the licence.
Thanks in advance!!