I'm attempting to wire up a REST API resource to use in my workflows, the service uses what I believe to be a fairly standard implementation of the Oauth2.0 client credentials flow. I've successfully authenticated with the service using Postman requests, and I've replicated it in retool using custom code, but I'm not able to get it working with Retool's provided implementation of the Oauth2.0 client credentials flow.
I've found several threads in this forum referencing the client credentials flow, none of which seem to have resolutions in which the flow actually works, the only solutions seem to be using a different auth flow, or implementing the client credentials flow yourself under the Cusom Auth system, so I'm not entirely sure retool's implementation of the client credentials flow is working for anyone (though, obviously it could be - people for whom it worked perfectly right away don't have a reason to post, I've just not seen any examples of someone having trouble with it finding a solution)
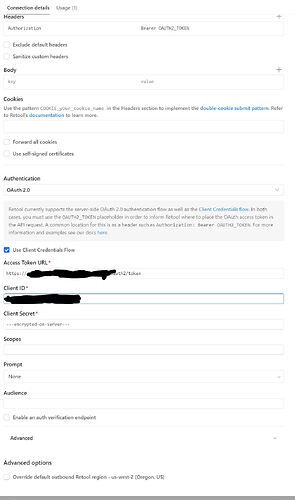
Here's a screenshot of how I've attempted to configure the resource:
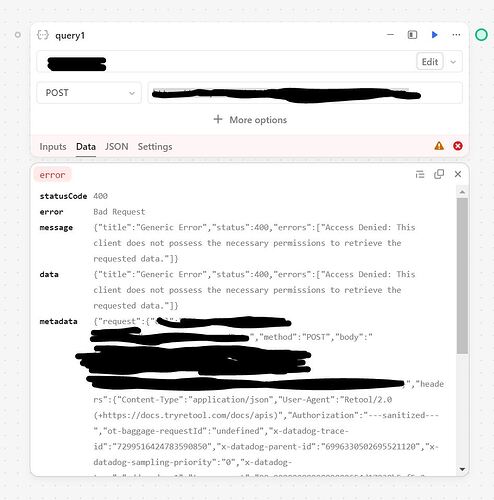
Here is a screenshot of my attempt to use the resource failing due to an auth-related error:
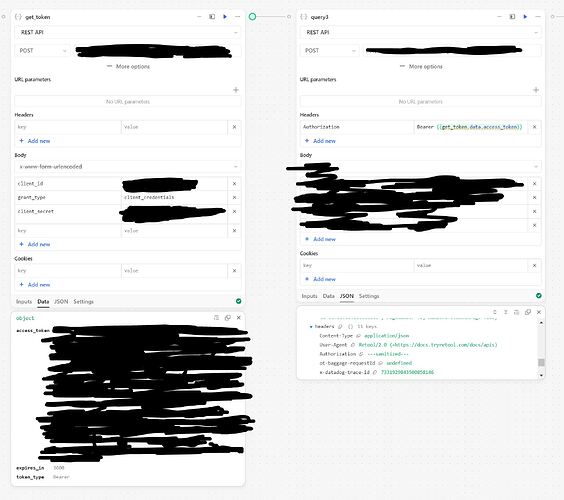
And here's the auth flow implemented successfully using RestAPI blocks:
Note that the credentials and URLs are exactly the same in my working example as in the failing ones, I'm sending the same credentials to the same auth endpoint, and calling the same API route with the resulting token.
I've tried playing around with the options a bit to try and get the resource working, but nothing I try seems to make a difference, and I'm not able to inspect the actual auth request to see what might be going wrong. It could be something very simple, like maybe retool's implementation is trying to use JSON encoding for the request body to the token endpoint, which requires x-www-form-urlencoded (not sure if that's standard or not, though I've seen plenty of other services use this encoding type for the token request, and I think the oauth 2.0 protocol is meant to be encoding agnostic so there ought to be a config option), but without any visibility into the token request I really can't identify the problem or propose a solution.
Switching it a custom auth implementation or building out my own flow using RestAPI blocks like above isn't difficult, but I'd like to be able to delegate that complexity to retool's off-the-shelf solution if possible, and I get the impression I'm not the only person to lose time trying to get the client-credentials flow to work, only to give up and find a workaround.
At a bare minimum, we should really be able to TEST the oauth 2.0 token request from the resource config page, like we can with Custom Auth, currently the only way to see if your resource is working properly is to use it in a workflow, and there isn't a way to see the details of the token request from there, so I have no idea if the sanitized value in my request headers is an actual bearer token, or some malformed value.