This is a brief introduction to how:
- Retool on-prem/self-hosted instance connects to an external API that uses SSL/TLS certification
- How to set up Retool on-prem to accept the External API's certificate.
Scenario: User's external API uses self-signed certificate, and Retool is throwing an error:
Error: self signed certificate in certificate chain
What's happening behind the in the backend:
- User triggers query within an app making a request to the API
- Query is sent from the app's frontend to the Retool's db-connector backend
- db-connector makes query request to API endpoint
- API sends a certificate that’s self-signed back to db-connector
- Retool goes up the certificate chain, and never finds a certificate it knows to trust (like from a certificate authority)
- Retool returns an error:
self-signed certificate
How to allow Retool to accept API’s self-signed certificate:
Create a Mount for API certificates:
- In the retool-onpremise directory, create a certs directory if it doesn't exist.
- Add your API certificate to the certs directory in a pem file
- This file can be a concatenated list of self-signed certificates
-
Add a mount from the path on the host to the db-connector container. For example with docker-compose, this would look like:
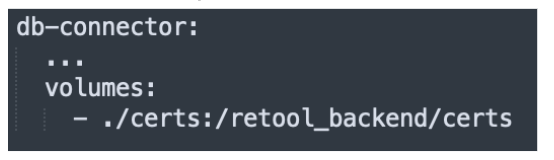
Point db-connector to your API certifications -
Enter your db-connector
-
Open docker.env
-
Add the environment variable NODE_EXTRA_CA_CERT and set the value to the path of your certificate file (from the container’s perspective, e.g.
/retool_backend/certs/cert.pem). -
Restart your containers for the changes to take effect
One method of creating a certification from your API:
Within your instance, run:
openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -sha256 -days 365
IMPORTANT: Make sure your Common Name (CN) matches your Retool instance’s domain or subdomain. If this doesn’t match you will receive an altname error. For example, for retool.domain.com, then the CN should match that or .domain.com.*