I have used retool for a year not but today all my apps failed because of ETIMEDOUT error. i deleted the old connection thinking it would solve anything but nothing. Anyone kindly help . thanks in advance
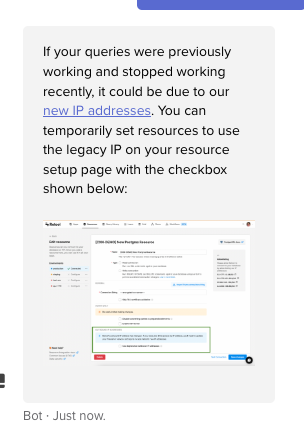
Hey @jakinda1! Can you take a look at the IP addresses you have whitelisted on your resource as mentioned here? As mentioned in the screenshot Scott shared there's also a checkbox you can use to switch to the legacy IPs for the moment. If neither of those options work let us know!
Hi,
I have the same problem, my ressource use SSH tunneling but Wpmudev doesn't support anymore SSH RSA 1, they say that nows the ssh key should be Ed25519.
Is there a way to get that with our Retool connections?
Hi!
Doesn't anybody have an idea about how I can connect a database throw SSH when rsa is forbidden?
(In French, I hope my English is clear and kind :-))
Is there something I can do to help to help me? ![]()
Hey @Floo!
Unfortunately, it looks like SSH keys are currently only generated using RSA the only workaround I'm aware of involves enabling RSA keys on the resource side (example). I'm personally not very familiar with Wpmudev and the only docs I'm finding suggest generating RSA keys as well - it may be helpful if you could share additional documentation you're referencing as context!
That being said, it sounds like the only solution at the moment might be to wait for a fix from our end. There's already an internal feature request open to support Ed25519 keys in SSH tunnels and we'll try an let you know here if it gets picked up and included!
Hi @Kabirdas,
Thank you for your answer !
Sorry for the delay in my response.
You are right for the RSA keys in the Wpmudev documentation.
But the support said me that about Retool Ed25519 keys :
If they don’t offer it, maybe there could be some newer cert SSH-RSA key as long as it’s not RSA 1 version – that should, theoretically, work fine too.
Is your RSA key is in version 1?
Ahh I see, yes, Retool currently uses RSA SHA-1 keys, the internal request is to upgrade from using that algorithm (folks over here are also aware of its known vulnerabilities). Sorry to not have a better answer for you!
Hi @Kabirdas,
Great to hear there is a ticket!
I asked to Wpmudev if they could relax their security rule for some months but they refused ![]()
So I have some apps and workflows that 100% does not work, it is not a little bug but the whole of functionalities from this ressource that are broken.
It is very problematic ![]()
At this time, I don't know if I have to move that stuff on another tool (no code or code) or if I should only wait but for how long?
I know it is hard to give but would you have an estimated time of arrival? ![]()
I understand Wpmudev because OpenSSH said in their release in on 2021-08-20:
In the SSH protocol, the "ssh-rsa" signature scheme uses the SHA-1
hash algorithm in conjunction with the RSA public key algorithm.
It is now possible[1] to perform chosen-prefix attacks against the
SHA-1 algorithm for less than USD$50K.
The [1] note refer to https://eprint.iacr.org/2020/014.pdf from 2020's!
I give you only caring motivation ![]()
(I hope my English is still clear and kind)
Hi!
Have you some news about it? ![]()
Hello @Floo ,
Thanks for your follow up here.
I can see the ticket is open on our end, but there is not a realistic delivery timeline available right now. I would suggest exploring alternatives if this issue remains urgent.
- Brett
Hi Brett,
Thank you for your transparency.
I'm relying heavily on low code to avoid technical bottlenecks while improving the reliability of our services.
But I spent a lot of time on this problem, with a monumental downgrade of an entire resource ![]()
That being said, I've taken the initiative and we've found a temporary solution to make an ssh tunnel on a vm of our own.
If someone of the community is interested, on our vm:
newuser=retool
sudo adduser $newuser
sudo mkdir /home/$newuser/.ssh/
sudo chmod 700 /home/$newuser/.ssh/
sudo chown $newuser:$newuser /home/$newuser/.ssh/
sudo su retool
ssh-keygen -t ed25519 -C "retool temporary key"
eval $(ssh-agent)
ssh-add
With the ed25519 key, we can access to Wpmudev from our vm.
After we add the Retool public key to let is access to the vm like it is well described here :
And the ssh tunnel creation:
ssh -N -f -L 127.0.0.1:3336:127.0.0.1:3306 retool@HOST-DESTINATION.COM
After we have only to update ressource to target the vm instead of the HOST-DESTINATION.
Have a nice week!