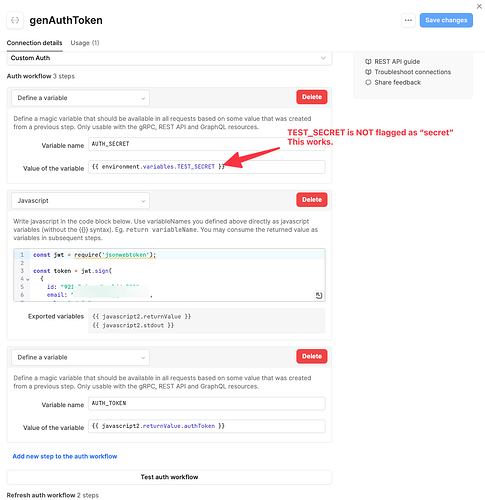
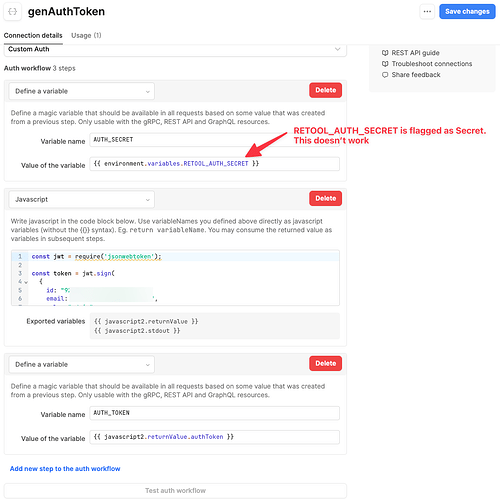
-
Context: I'm using custom auth to generate a jwt token using a secret I saved as environment variable in Retool Cloud (Settings > Configuration variables)
-
Steps: I followed the steps outlined in the docs.
-
Problem: If I save an environment variable as a secret, it's not read in the JS and the resulting generated token will be invalid. If I do save the same variable and I don't flag it as a secret, the generated token will be valid and everything will work. The problem is that I want to "flag" the variable as secret and the tooltip when flagging clearly says that I would be able to use it only in resources as workflows (which is fine by me since custom auth in the resource's settings). I obviously tired to revoke the variables in the custom auth but nothing changed.
-
Screenshots:
Hey @Jack_Re! Thanks for reaching out.
This is kind of an interesting use case. Ultimately, it's not working for you because any variable flagged as a secret is encrypted server-side and thus never exposed to the client. The JavaScript block that you've defined as part of this custom authentication flow executes client-side and thus will never be able to access secrets.
Ok got it @Darren thanks for the reply! It wasn't clear to me that the custom-auth JS block was executed client-side.
So if I take the exact same JS code and run it in a workflow, it will work (assuming that I refer to the secret with retoolContext.configVars), given that the JS code is executed server-side, correct?
It's not made very clear, in general! And yes - a JS block within a workflow will execute server-side and shouldn't run into any issues. ![]()
Tested, works ![]() Thanks @Darren!
Thanks @Darren!
Hey @Jack_Re - glad to hear that it's working!
For whatever reason, my mind wasn't satisfied with the way this was resolved and kept returning to it. ![]() I decided to do some additional testing and am now pretty confident that my initial response isn't quite correct.
I decided to do some additional testing and am now pretty confident that my initial response isn't quite correct.
Most notably, JS blocks in a custom auth flow definitely run in a Node environment. What's particularly odd is that everything seems to work now. I'm able to reference and read secrets in both JS and variable blocks. I don't think any updates made a targeted change to this behavior, but I'll reach out to the team in order to confirm.
There's no urgent reason to update your implementation, unless you'd rather save your workflow runs for something else, but I thought I'd let you know!
Thanks a lot @Darren , I really appreciate it!
Great to know that the custom code runs server-side! nonetheless, I tried to re-run it, and it still doesn’t work for me, while the same code generates a valid token if I use a variable not flagged as secret or if run via workflow.
I don't mind it using workflows for now, but I'd rather prefer using custom auth since using a workflow to authenticate a resource doesn't seem optimal so if there's a (secure) way to read secrets in JS blocks in custom auth, it would be great.